Your Digital Life Protecting Your Privacy
Understanding the Digital Footprint You Leave
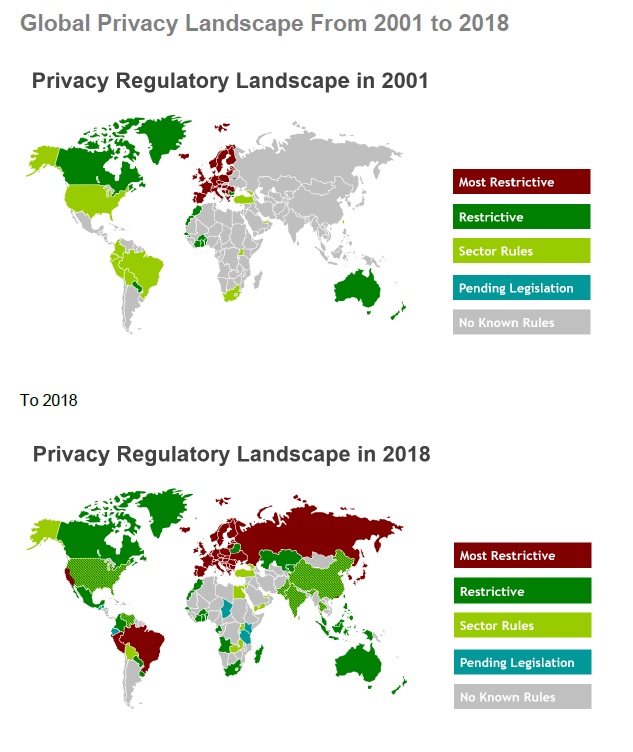
We live in a hyper-connected world. Every online interaction, from searching for a recipe to posting a photo, leaves a digital footprint. This footprint comprises data points about your activities, preferences, and even your location. Understanding the breadth and depth of this footprint is crucial to protecting your privacy. It’s more than just your social media posts; it includes your browsing history, online purchases, app usage, and even the metadata embedded in your photos. The more aware you are of this data trail, the better equipped you are to manage it.
Securing Your Passwords and Accounts
Strong, unique passwords are the foundation of online security. Avoid using easily guessable information like birthdays or pet names. Instead, opt for complex passwords combining uppercase and lowercase letters, numbers, and symbols. Consider using a password manager to generate and securely store these passwords. This eliminates the need to remember countless complicated combinations and helps prevent the catastrophic consequences of a single password breach impacting multiple accounts. Enable two-factor authentication (2FA) wherever possible; this adds an extra layer of security, requiring a second verification method beyond your password, such as a code sent to your phone.

The Importance of Privacy Settings on Social Media
Social media platforms are data goldmines. Review and adjust your privacy settings regularly. Limit the visibility of your posts, photos, and information to friends and family, or even a more select group of trusted contacts. Be cautious about sharing personal information, such as your address, phone number, or workplace, directly on your profile. Think critically before accepting friend requests from strangers, and be wary of public posts that could be used to piece together more information about you. Remember that even seemingly innocuous information can be exploited to target you.
Safeguarding Your Data on Mobile Devices
Smartphones and tablets are personal data repositories. Install strong passcodes or use biometric authentication (fingerprint or facial recognition) to protect your device. Regularly update your operating system and apps to patch security vulnerabilities. Be selective about which apps you download, avoiding those from untrusted sources. Pay close attention to app permissions, granting only the access necessary for the app to function correctly. Consider using a virtual private network (VPN) when using public Wi-Fi to encrypt your internet traffic and protect your data from interception.
Protecting Your Online Shopping Privacy
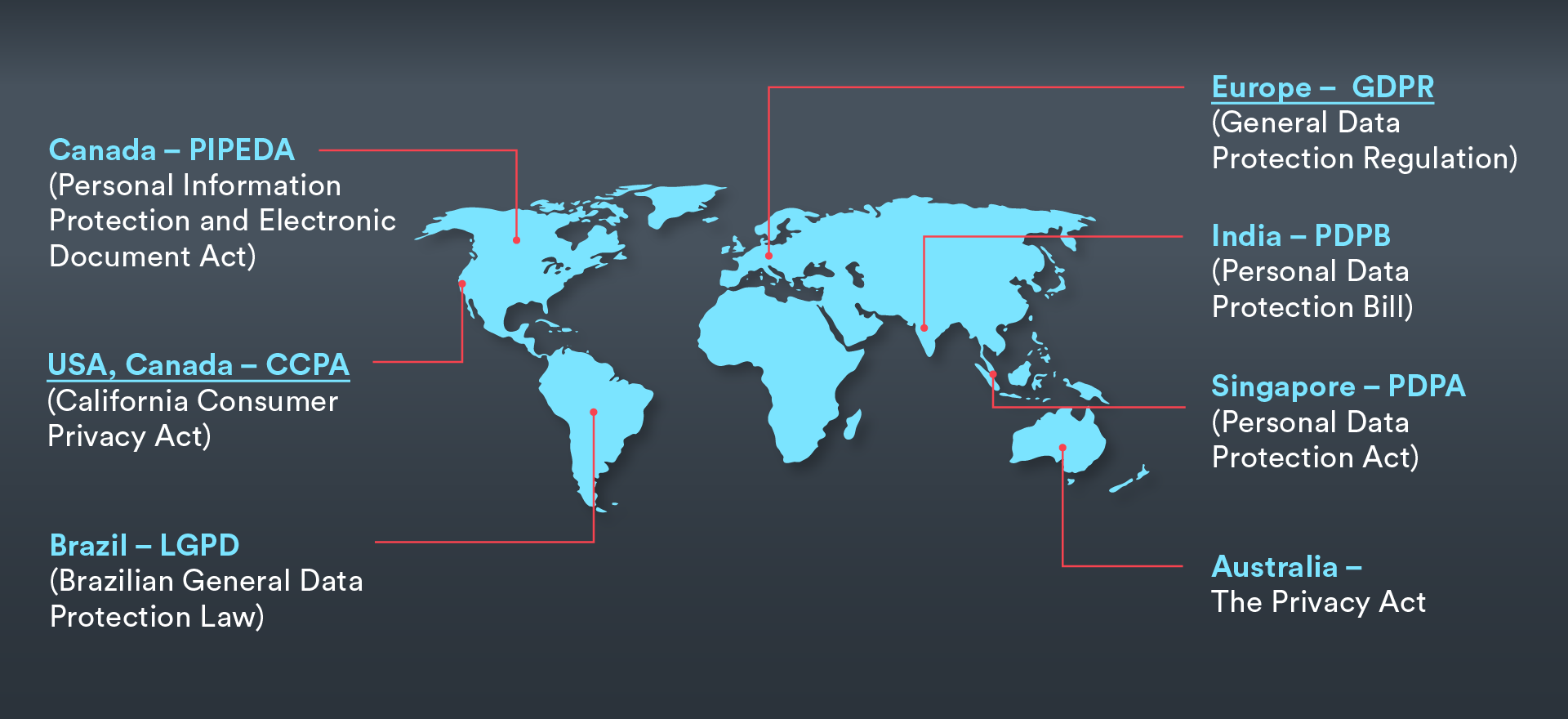
Online shopping offers incredible convenience, but it also comes with privacy risks. Only shop on secure websites (look for “https” in the URL). Be cautious about entering your credit card information on unfamiliar sites. Use strong passwords and consider using a virtual credit card or prepaid card for online purchases to limit your liability in case of a breach. Regularly review your bank and credit card statements to detect any unauthorized transactions. Understand your rights under data protection laws and know how to report suspicious activity.
Being Mindful of Online Tracking and Cookies
Websites and advertisers use cookies and other tracking technologies to collect data about your browsing habits.